the exemption list stuck. TailBite itself but also triggers alarm. Only TailBite
manager is clean
greetings
Thomas
Moderators: gnozal, ABBKlaus, lexvictory
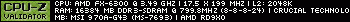
Avira 8 PersonalABBKlaus wrote:What scanner are you using ?
Code: Select all
Datei TBUpdater.exe empfangen 2008.05.23 23:41:48 (CET)
Ergebnis: 5/32 (15.63%)
Antivirus Version letzte aktualisierung Ergebnis
AhnLab-V3 2008.5.22.1 2008.05.23 -
AntiVir 7.8.0.19 2008.05.23 TR/Crypt.XPACK.Gen
Authentium 5.1.0.4 2008.05.23 -
Avast 4.8.1195.0 2008.05.23 -
AVG 7.5.0.516 2008.05.23 -
BitDefender 7.2 2008.05.23 -
CAT-QuickHeal 9.50 2008.05.23 (Suspicious) - DNAScan
ClamAV 0.92.1 2008.05.23 -
DrWeb 4.44.0.09170 2008.05.23 -
eSafe 7.0.15.0 2008.05.22 -
eTrust-Vet 31.4.5817 2008.05.23 -
Ewido 4.0 2008.05.23 -
F-Prot 4.4.4.56 2008.05.23 -
F-Secure 6.70.13260.0 2008.05.23 -
Fortinet 3.14.0.0 2008.05.23 -
GData 2.0.7306.1023 2008.05.23 -
Ikarus T3.1.1.26.0 2008.05.23 -
Kaspersky 7.0.0.125 2008.05.23 -
McAfee 5302 2008.05.23 -
Microsoft 1.3520 2008.05.23 -
NOD32v2 3128 2008.05.23 -
Norman 5.80.02 2008.05.23 -
Panda 9.0.0.4 2008.05.23 Suspicious file
Prevx1 V2 2008.05.23 Malicious Software
Rising 20.45.42.00 2008.05.23 -
Sophos 4.29.0 2008.05.23 -
Sunbelt 3.0.1123.1 2008.05.17 -
Symantec 10 2008.05.23 -
TheHacker 6.2.92.318 2008.05.23 -
VBA32 3.12.6.6 2008.05.23 -
VirusBuster 4.3.26:9 2008.05.23 -
Webwasher-Gateway 6.6.2 2008.05.23 Trojan.Crypt.XPACK.Gen
Code: Select all
Datei UpdateTool.exe empfangen 2008.05.20 20:35:17 (CET)
Status: Beendet
Ergebnis: 11/32 (34.38%)
Antivirus Version letzte aktualisierung Ergebnis
AhnLab-V3 2008.5.20.0 2008.05.20 -
AntiVir 7.8.0.19 2008.05.20 TR/Crypt.XPACK.Gen
Authentium 5.1.0.4 2008.05.19 -
Avast 4.8.1195.0 2008.05.20 -
AVG 7.5.0.516 2008.05.20 Generic10.ZBL
BitDefender 7.2 2008.05.20 -
CAT-QuickHeal 9.50 2008.05.19 -
ClamAV 0.92.1 2008.05.20 -
DrWeb 4.44.0.09170 2008.05.20 -
eSafe 7.0.15.0 2008.05.20 Win32.Monder.gen
eTrust-Vet 31.4.5806 2008.05.20 -
Ewido 4.0 2008.05.20 -
F-Prot 4.4.2.54 2008.05.16 -
F-Secure 6.70.13260.0 2008.05.20 Trojan.Win32.Monder.gen
Fortinet 3.14.0.0 2008.05.20 W32/Monder!tr
GData 2.0.7306.1023 2008.05.20 Trojan.Win32.Monder.gen
Ikarus T3.1.1.26.0 2008.05.20 Virus.Trojan.Win32.Monder
Kaspersky 7.0.0.125 2008.05.20 Trojan.Win32.Monder.gen
McAfee 5299 2008.05.20 -
Microsoft 1.3520 2008.05.20 -
NOD32v2 3114 2008.05.20 -
Norman 5.80.02 2008.05.20 -
Panda 9.0.0.4 2008.05.20 -
Prevx1 V2 2008.05.20 -
Rising 20.45.12.00 2008.05.20 -
Sophos 4.29.0 2008.05.20 Mal/Generic-A
Sunbelt 3.0.1123.1 2008.05.17 -
Symantec 10 2008.05.20 -
TheHacker 6.2.92.314 2008.05.20 -
VBA32 3.12.6.6 2008.05.20 Trojan.Win32.Monder.gen
VirusBuster 4.3.26:9 2008.05.20 -
Webwasher-Gateway 6.6.2 2008.05.20 Trojan.Crypt.XPACK.Gen
You mean PROXY? Routers and Firewalls are automatically passed by OpenNetworkConnection(), if permission allowed. Only HTTP-Proxies must be handled manually.ABBKlaus wrote:won´t work behind a corporate firewall
Code: Select all
onErrorGoto(?Fred)